Configuring a Global Shared Secret for DevOps or Jira Integration Authentication
Security is a top priority, and you may not want authentication credentials for your DevOps or Jira instances to be distributed across your organization. As an administrator, you can securely store tokens or secrets in a central location, allowing users to access integrated systems without needing to know or handle sensitive details directly.
By using shared global secrets, you can safely store credentials such as usernames, passwords, tokens, and client identifiers in Fluid’s Key Vault.
When configuring an integration, users can simply enable the “Use Shared Secret” option in their setup. Fluid will automatically retrieve and apply the appropriate credentials when connecting to your external systems, ensuring secure and seamless authentication.
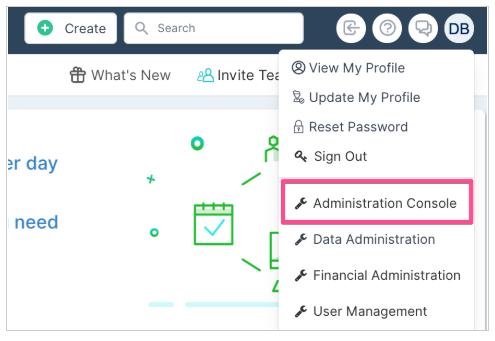
From the drop down menu under your avatar select Administration Console.
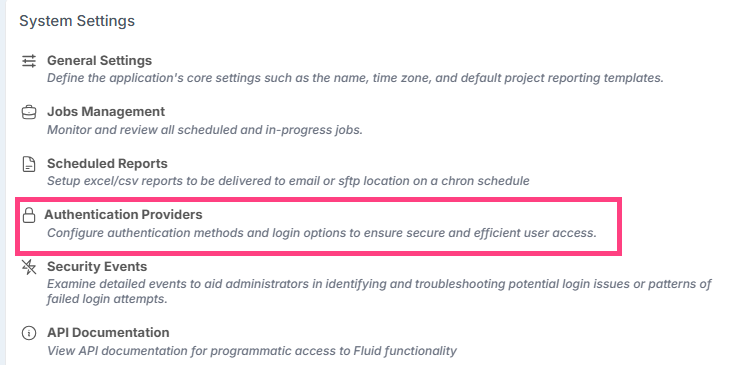
- Select Authentication Providers
- Enable "Use Global Integration Shared Secret"
DevOps
Azure DevOps supports two authentication methods for integration:
Personal Access Token (PAT)
Azure AD Service Principal Authentication Token
To configure authentication:
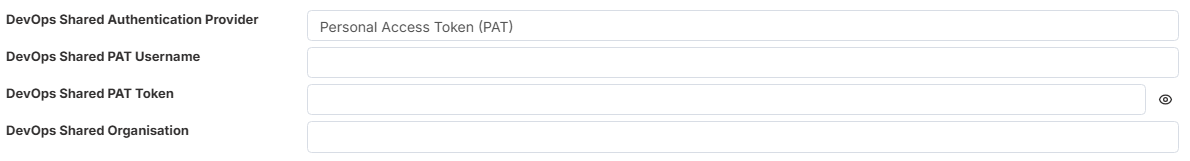
Click DevOps Shared Authentication Provider.
Select your preferred authentication method — either Personal Access Token or Service Principal.
Enter the required credentials or tokens as prompted to complete the setup.
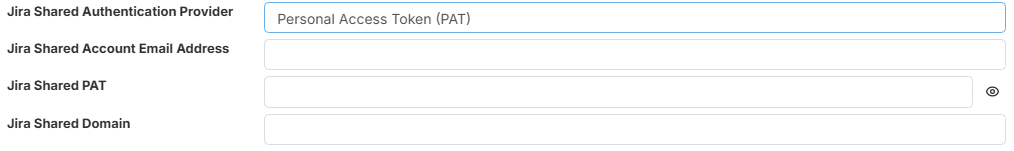
- Personal Access Token (PAT)
Details on how to generate a PAT token from DevOps can be found here.
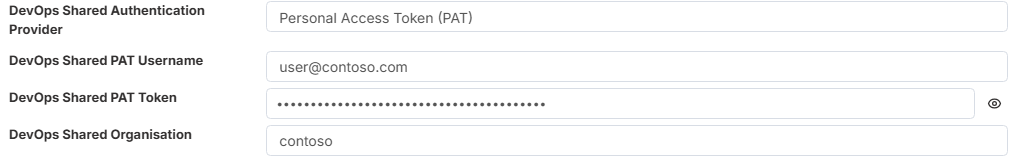
DevOps Shared PAT Username - This is the username associated with the Personal Access Token (PAT) generated from Azure DevOps. It is typically the email address of the account used to create the token (for example: user@company.com).
DevOps Shared PAT Token - This is the character string representing the Personal Access Token (PAT) generated in Azure DevOps. When copying and pasting the token into this field, ensure there are no leading or trailing spaces.
DevOps Shared Organisation - This refers to your Azure DevOps organization name. You can find it in the URL of your DevOps instance:
For example, in https://contoso.visualstudio.com/, the organization name is contoso.
If your URL follows the newer format, such as https://dev.azure.com/contoso/, the organization name remains contoso.
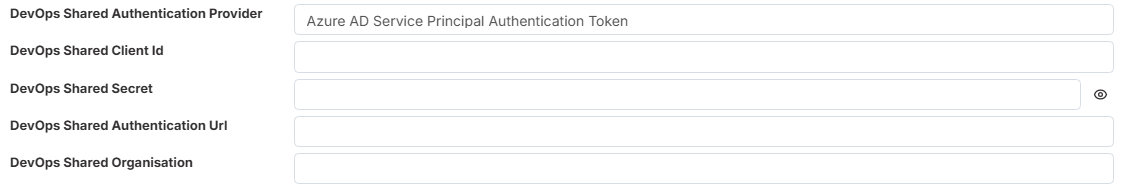
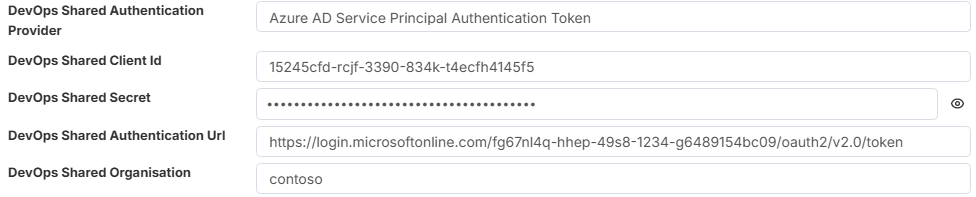
- Azure AD Service Principal Authentication Token
DevOps Shared Client Id - The unique client ID GUID for the service principal
DevOps Shared Secret - The client secret.
DevOps Shared Authentication Url - https://login.microsoftonline.com/{ Azure Tenant ID}/oauth2/v2.0/token.
An { Azure Tenant ID } is a unique GUID (Globally Unique Identifier) that represents your Microsoft Entra ID (Azure AD) instance, your organization’s identity directory in Azure.Every company or organization that uses Microsoft cloud services (like Azure, Microsoft 365, or Azure DevOps) automatically has a tenant.
The Tenant ID identifies that directory across all Microsoft cloud services
DevOps Shared Organisation - This refers to your Azure DevOps organization name. You can find it in the URL of your DevOps instance:
For example, in https://contoso.visualstudio.com/, the organization name is contoso.
If your URL follows the newer format, such as https://dev.azure.com/contoso/, the organization name remains contoso.
NOTE: When configuring permissions for the Service Principal in Azure DevOps, ensure that it has access not only to the project level but also to the Area Path in which the project resides. The Service Principal must have permissions that cascade through the hierarchy down to the specific project level.
The Service Principal should be granted the same level of access as a typical user who contributes to boards or work items within Azure DevOps. This ensures it can perform all necessary integration actions.
For more details on configuring Service Principals in Azure DevOps, refer to the official Microsoft documentation:
Details on Service Principals : https://learn.microsoft.com/en-us/azure/devops/integrate/get-started/authentication/service-principal-managed-identity?view=azure-devops#1-create-a-new-managed-identity-or-application-service-principal
Jira
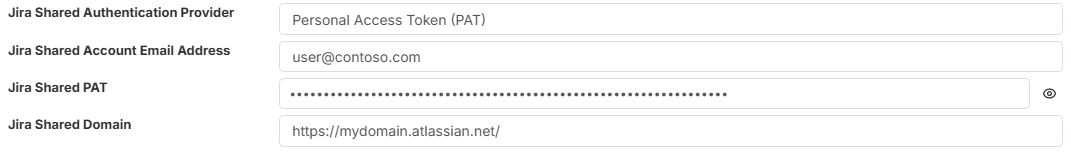
Details on how to generate a PAT token from Jira can be found here.
Jira Shared Account email address - This is the email address associated with the account and Personal Access Token (PAT) generated from Jira. It is typically the email address of the account used to create the token (for example: user@company.com).
Jira Shared PAT Token - This is the character string representing the Personal Access Token (PAT) generated in Jira. When copying and pasting the token into this field, ensure there are no leading or trailing spaces.
Jira Shared Domain - The url of the domain of your Jira instance, eg
https://your_domain.atlassian.net/
- click Save
Using Global Secrets
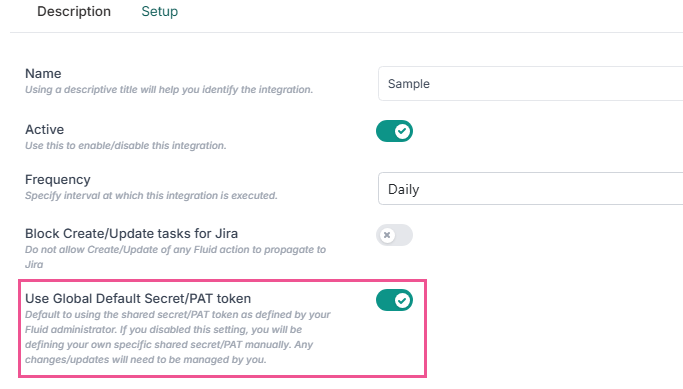
When configuring a board for integration to use global shared secrets for authentication, ensure the config toggle "Use Global Default Secret/PAT token" is enabled